In this post I’ll share how I crafted the perfect pentest note template for my needs.
I experimented with many ways of taking notes during penetration tests. Like many pentesters, I started with CherryTree, but I always felt it was holding me back from being more productive. Its limitations made note-taking frustrating and, ultimately, my notes suffered. I soon switched to a simple text file—quick, easy, and accessible on any machine—but it lacked syntax highlighting. Since I was already familiar with Markdown, I began searching for a good Markdown editor. After trying several, I discovered Obsidian: easy to use, with a simple yet effective UI. Now I could take notes rapidly, using just my keyboard, without sacrificing essential features like syntax highlighting or document organization.
Note-taking during a penetration test is crucial for crafting a comprehensive report afterward. Yet, it also supports real-time work during the pentest itself. After conducting numerous tests, I developed my own note-taking template to streamline the process. The template is in Markdown format, which means you can paste it into any Markdown editor—or even into Notion. It covers all the necessary details about the pentest, its scope, and the organizational environment around the test.
Additionally, it includes frequently used commands for the initial discovery phase, ensuring that no step is missed while keeping all results neatly stored.
The template retains all essential information without being over-engineered—it’s simple enough to adapt to any pentest without becoming annoyingly complicated. Plus, most Markdown editors allow you to collapse and expand headlines, so you can hide sections you no longer need.
This is how it could look like in a Markdown editor:
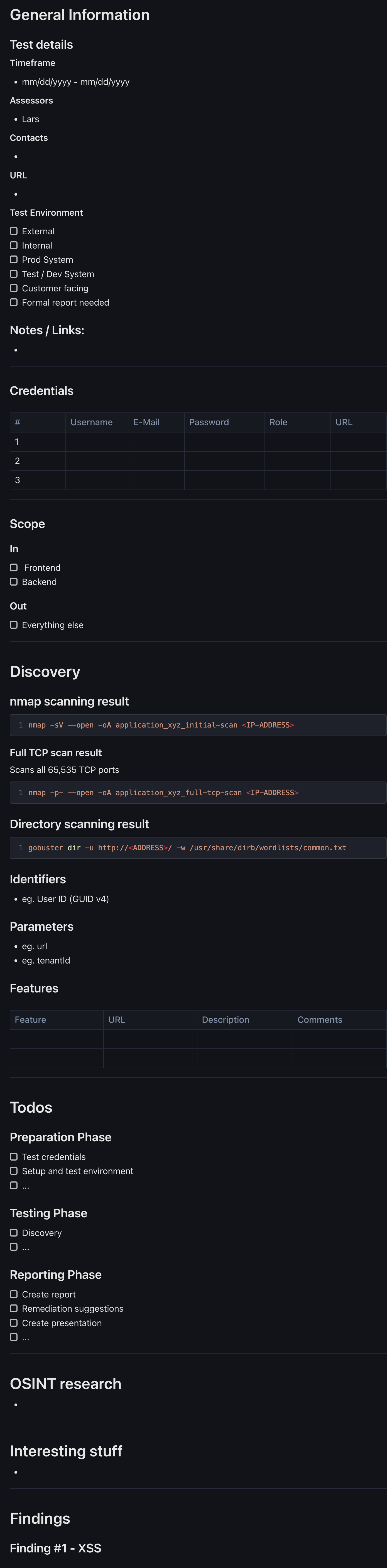
You can find the full template in Markdown below. Feel free to copy it and adjust it for your own needs.
# Pentest - <Name of the Pentest>
# General Information
## Test Details
**Timeframe**
* mm/dd/yyyy - mm/dd/yyyy
**Assessors**
* Lars
**Contacts**
* \
**URL / URI**
* \
**Test Environment**
- [ ] External
- [ ] Internal
- [ ] Prod System
- [ ] Test / Dev System
- [ ] Customer facing
- [ ] Formal report needed
## **Notes / Links:**
* \
---
## Credentials
| # | Username | E-Mail | Password | Role | URL |
|----|----|----|----|----|----|
| 1 | | | | | |
| 2 | | | | | |
| 3 | | | | | |
---
## Scope
### In
- [ ] Frontend
- [ ] Backend
- [ ] ...
### Out
- [ ] Infrastructure
- [ ] ...
- [ ] Everything else
---
# Discovery
## nmap scanning result
`nmap -sV --open -oA application_xyz_initial-scan <IP-ADDRESS>`
### Full TCP scan result
Scan for any services running on non-standard ports that the initial scan may have missed. Since this scans all 65,535 TCP ports, it can take a long time to finish depending on the network.
`nmap -p- --open -oA application_xyz_full-tcp-scan <IP-ADDRESS>`
## Directory scanning result
`gobuster dir -u http://<ADDRESS>/ -w /usr/share/dirb/wordlists/common.txt`
## Identifiers
* eg. User ID (GUID v4)
## Parameters
* eg. url
* eg. tenantId
## Features
| Feature | URL | Description | Comments |
|----|----|----|----|
| | | | |
| | | | |
---
# Todos
## Preparation Phase
- [ ] Test credentials
- [ ] Setup and test environment
- [ ] ...
## Testing Phase
- [ ] Discovery
- [ ] ...
### Insert Checklist for OWASP Top 10 / OWASP API Top 10 / ...
- [ ] ...
## Reporting Phase
- [ ] Create report
- [ ] Remediation suggestions
- [ ] Create presentation
- [ ] ...
---
# OSINT Research
* \
---
# Interesting Stuff
* \
---
# Findings
## Finding #1 - XSS

